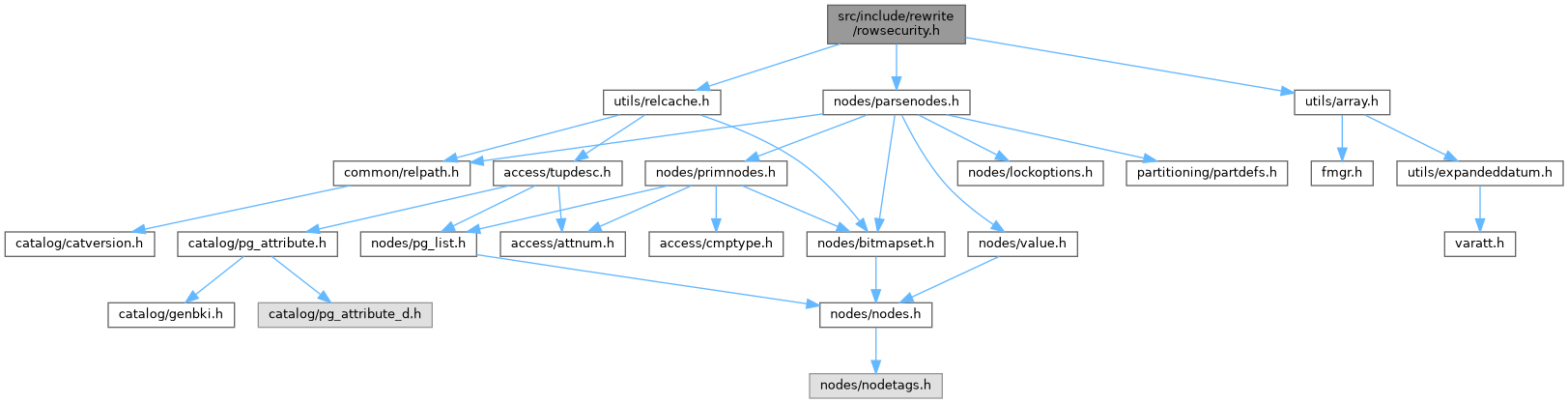
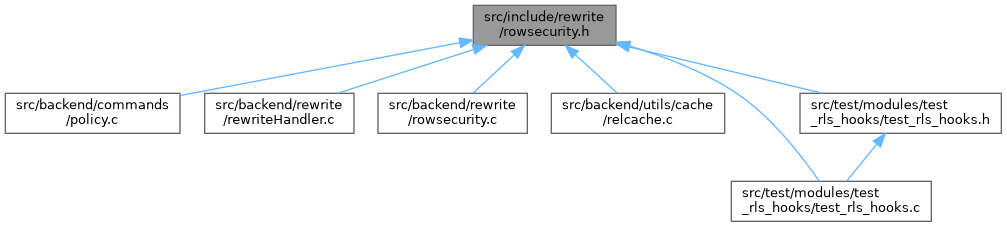
Definition at line 98 of file rowsecurity.c.
101{
109
110
113 *hasRowSecurity = false;
115
117
118
121 return;
122
124
125
128
129
131
132
134 return;
135
136
137
138
139
140
142 {
143
144
145
146
147
148 *hasRowSecurity = true;
149
150 return;
151 }
152
153
154
155
156
157
158
159
160
161
163
164 commandType = rt_index ==
root->resultRelation ?
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
196 {
199
203
209 }
210
211
212
213
214
215
216
217
220
229
230
231
232
233
234
235
236
237
238
239
243 {
246
250
256 }
257
258
259
260
261
262
263
265 {
266
268
277
278
279
280
281
282
283
284
286 {
289
301 }
302
303
304
305
306
307
311 {
316
318 {
319
320
321
322
326
327
328
329
330
331
332
339 true);
340 }
341
342
343
344
345
346
347
348
350 {
360 true);
361 }
362
363
364
365
366
368 {
369
376 false);
377
378
379
380
381
382
383
391 true);
392 }
393 }
394 }
395
396
397
398
399
400
401
402
403
404
405
406
407
408
409
410
411
412
413
414
415
416
417
418
420 {
429
430
431
432
433
437
438
439
440
441
448 true);
449
450
457 false);
458
459
460
461
462
463
465 {
475 true);
476 }
477
478
479
480
481
485
486
487
488
489
496 true);
497
498
499
500
501
502
506
513 false);
514
515
516
517
518
519
520
528 true);
529 }
530
532
533
534
535
536
539
540
541
542
543
544 *hasRowSecurity = true;
545}
#define Assert(condition)
#define OidIsValid(objectId)
RTEPermissionInfo * getRTEPermissionInfo(List *rteperminfos, RangeTblEntry *rte)
@ WCO_RLS_MERGE_UPDATE_CHECK
@ WCO_RLS_MERGE_DELETE_CHECK
void setRuleCheckAsUser(Node *node, Oid userid)
int check_enable_rls(Oid relid, Oid checkAsUser, bool noError)
static void add_with_check_options(Relation rel, int rt_index, WCOKind kind, List *permissive_policies, List *restrictive_policies, List **withCheckOptions, bool *hasSubLinks, bool force_using)
static void get_policies_for_relation(Relation relation, CmdType cmd, Oid user_id, List **permissive_policies, List **restrictive_policies)
static void add_security_quals(int rt_index, List *permissive_policies, List *restrictive_policies, List **securityQuals, bool *hasSubLinks)
void table_close(Relation relation, LOCKMODE lockmode)
Relation table_open(Oid relationId, LOCKMODE lockmode)
References ACL_SELECT, ACL_UPDATE, add_security_quals(), add_with_check_options(), Assert, check_enable_rls(), CMD_DELETE, CMD_INSERT, CMD_MERGE, CMD_SELECT, CMD_UPDATE, fb(), get_policies_for_relation(), getRTEPermissionInfo(), GetUserId(), NIL, NoLock, OidIsValid, ONCONFLICT_SELECT, ONCONFLICT_UPDATE, RLS_NONE, RLS_NONE_ENV, root, RTE_RELATION, setRuleCheckAsUser(), table_close(), table_open(), WCO_RLS_CONFLICT_CHECK, WCO_RLS_INSERT_CHECK, WCO_RLS_MERGE_DELETE_CHECK, WCO_RLS_MERGE_UPDATE_CHECK, and WCO_RLS_UPDATE_CHECK.
Referenced by fireRIRrules().