Loading...
Searching...
No Matches
sasl.h File Reference
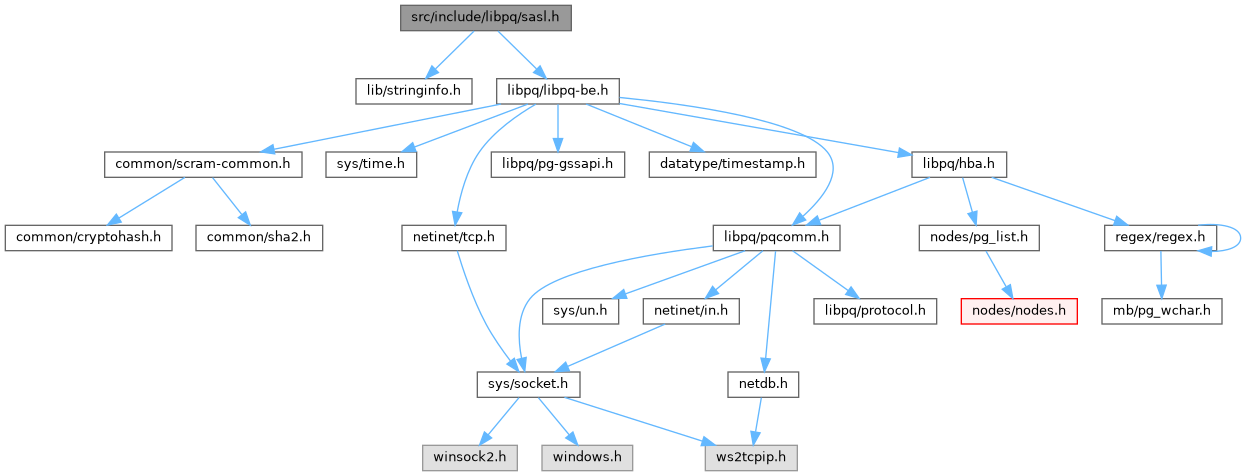
Include dependency graph for sasl.h:
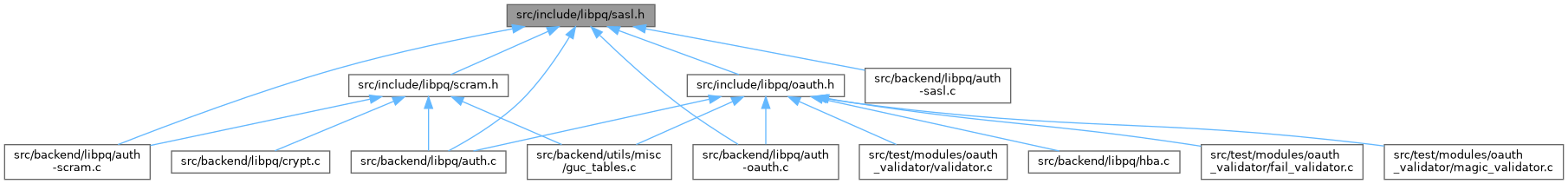
This graph shows which files directly or indirectly include this file:
Go to the source code of this file.
Data Structures | |
| struct | pg_be_sasl_mech |
Macros | |
| #define | PG_SASL_EXCHANGE_CONTINUE 0 |
| #define | PG_SASL_EXCHANGE_SUCCESS 1 |
| #define | PG_SASL_EXCHANGE_FAILURE 2 |
| #define | PG_MAX_SASL_MESSAGE_LENGTH 1024 |
Typedefs | |
| typedef struct pg_be_sasl_mech | pg_be_sasl_mech |
Functions | |
| int | CheckSASLAuth (const pg_be_sasl_mech *mech, Port *port, char *shadow_pass, const char **logdetail) |
Macro Definition Documentation
◆ PG_MAX_SASL_MESSAGE_LENGTH
◆ PG_SASL_EXCHANGE_CONTINUE
◆ PG_SASL_EXCHANGE_FAILURE
◆ PG_SASL_EXCHANGE_SUCCESS
Typedef Documentation
◆ pg_be_sasl_mech
Function Documentation
◆ CheckSASLAuth()
|
extern |
Definition at line 44 of file auth-sasl.c.
46{
55 int result;
57
58 /*
59 * Send the SASL authentication request to user. It includes the list of
60 * authentication mechanisms that are supported.
61 */
63
65 /* Put another '\0' to mark that list is finished. */
67
70
71 /*
72 * Loop through SASL message exchange. This exchange can consist of
73 * multiple messages sent in both directions. First message is always
74 * from the client. All messages from client to server are password
75 * packets (type 'p').
76 */
78 do
79 {
80 pq_startmsgread();
83 {
84 /* Only log error if client didn't disconnect. */
86 {
90 mtype)));
91 }
92 else
94 }
95
96 /* Get the actual SASL message */
99 {
100 /* EOF - pq_getmessage already logged error */
103 }
104
106
107 /*
108 * The first SASLInitialResponse message is different from the others.
109 * It indicates which SASL mechanism the client selected, and contains
110 * an optional Initial Client Response payload. The subsequent
111 * SASLResponse messages contain just the SASL payload.
112 */
114 {
116
118
119 /*
120 * Initialize the status tracker for message exchanges.
121 *
122 * If the user doesn't exist, or doesn't have a valid password, or
123 * it's expired, we still go through the motions of SASL
124 * authentication, but tell the authentication method that the
125 * authentication is "doomed". That is, it's going to fail, no
126 * matter what.
127 *
128 * This is because we don't want to reveal to an attacker what
129 * usernames are valid, nor which users have a valid password.
130 */
132
136 else
138
140 }
141 else
142 {
145 }
147
148 /*
149 * The StringInfo guarantees that there's a \0 byte after the
150 * response.
151 */
153
154 /*
155 * Hand the incoming message to the mechanism implementation.
156 */
159 logdetail);
160
161 /* input buffer no longer used */
163
165 {
166 /*
167 * PG_SASL_EXCHANGE_FAILURE with some output is forbidden by SASL.
168 * Make sure here that the mechanism used got that right.
169 */
172
173 /*
174 * Negotiation generated data to be sent to the client.
175 */
177
180 else
182
184 }
186
187 /* Oops, Something bad happened */
189 {
191 }
192
194}
void sendAuthRequest(Port *port, AuthRequest areq, const void *extradata, int extralen)
Definition auth.c:677
FILE * input
Definition stringinfo.h:47
References appendStringInfoChar(), Assert, AUTH_REQ_SASL, AUTH_REQ_SASL_CONT, AUTH_REQ_SASL_FIN, buf, DEBUG4, elog, ereport, errcode(), ERRCODE_PROTOCOL_VIOLATION, errmsg(), ERROR, fb(), initStringInfo(), input, output, pfree(), PG_SASL_EXCHANGE_CONTINUE, PG_SASL_EXCHANGE_FAILURE, PG_SASL_EXCHANGE_SUCCESS, port, pq_getbyte(), pq_getmessage(), pq_getmsgbytes(), pq_getmsgend(), pq_getmsgint(), pq_getmsgrawstring(), pq_startmsgread(), PqMsg_SASLResponse, sendAuthRequest(), STATUS_EOF, STATUS_ERROR, and STATUS_OK.
Referenced by CheckPWChallengeAuth(), and ClientAuthentication().